- Ask yourself the question, what’s my compliance policy for the company, HIPPA, PCI, SOX, DISA, STIG, etc…
- Have I spoken to my internal audit staff?
- Have I spoken to my security team yet?
Step 1 – Collaborate with Security
I almost want to write a book on ‘How to be successful at Virtual Security’ and step one of that book would include collaborating with your security department to craft a security policy document that describes the methods that will be used to secure the virtual infrastructure. Let’s face it, securing your VMware Infrastructure isn’t easy.

this isn’t easy folks
Partnering with your security team upfront vs. designing this yourself and waiting for their blessing after the fact will yield completely different results. I think you’ll find that the collaborative method will not only surprise them but go along way in the secure design and crafting of a good security policy document, which ultimately can be used for both internal and external audit representatives as a roadmap for showing your work.
Step 2 – Define Your Configuration Policy
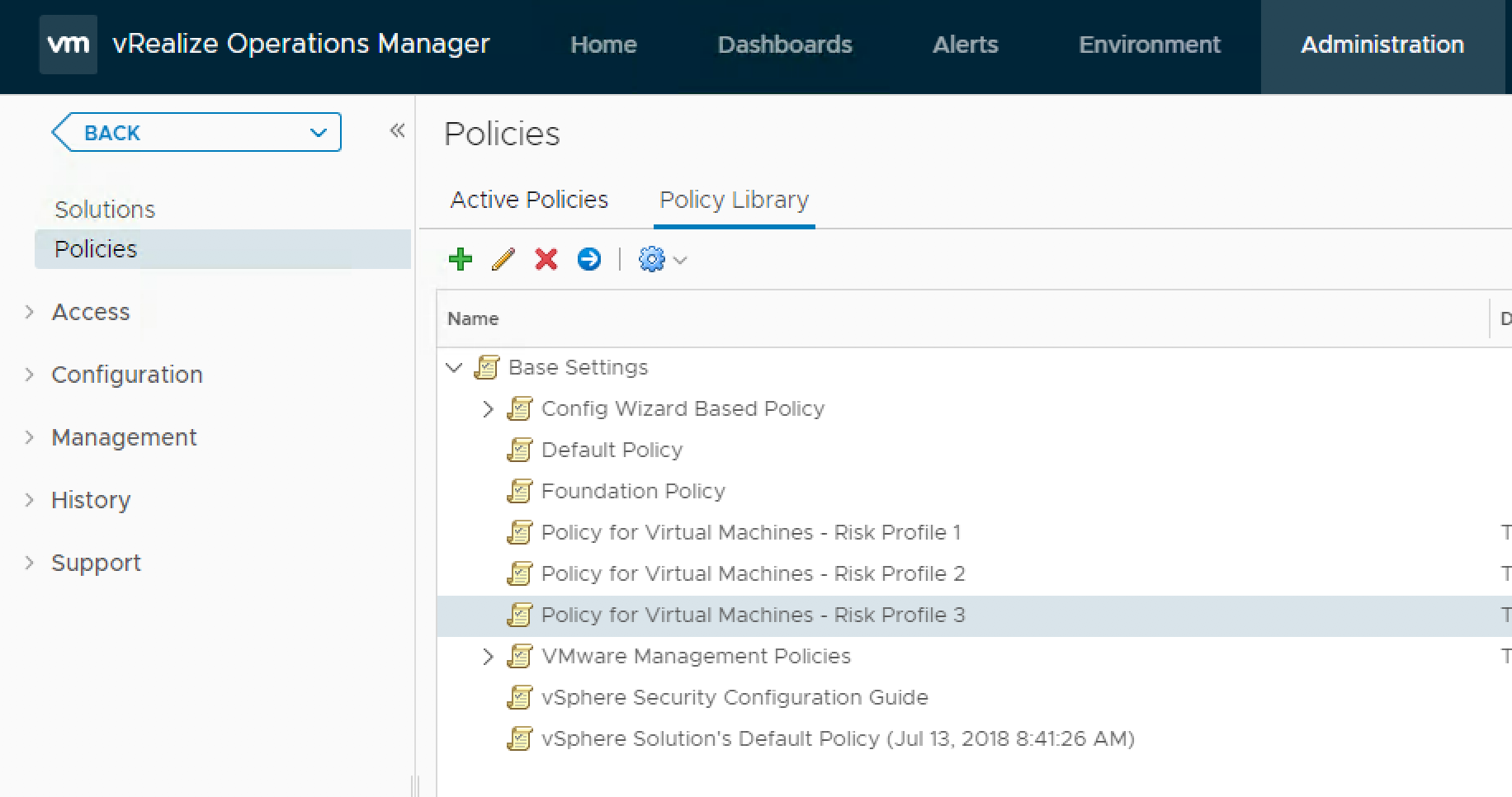
 I would start by reviewing all Risk Profile 3 options and determining how many if not all should be configured for you environment. Then move onto RP2 and eventually RP1 options depending on your acceptable risk for your environment. Examples could be something like the following:
I would start by reviewing all Risk Profile 3 options and determining how many if not all should be configured for you environment. Then move onto RP2 and eventually RP1 options depending on your acceptable risk for your environment. Examples could be something like the following:All vSphere environments containing PCI data or DMZ workloads will have RP2 settings implemented, all other environments will have RP1 settings applied
Step 3 – Choose Your Tools
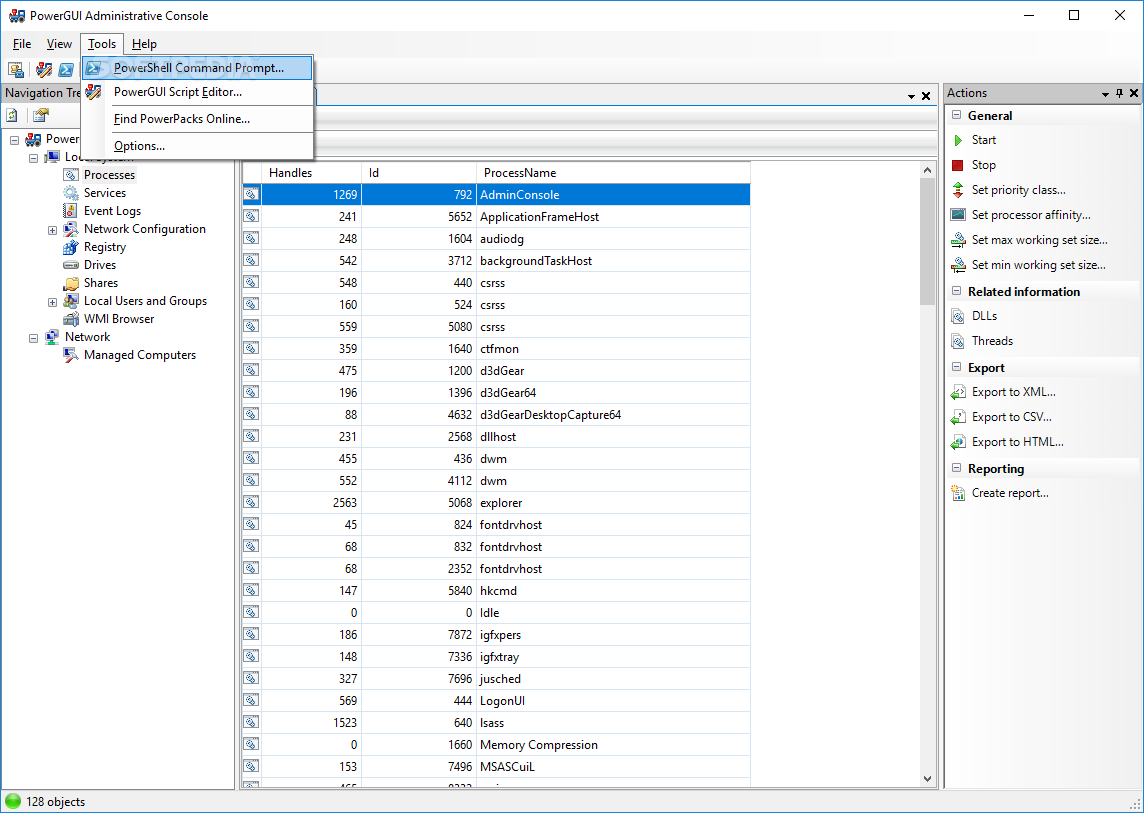
PowerGUI
This tool isn’t really being supported anymore, but for those that like a GUI like interface, this little gem can help you build out PowerCLI scripts from the samples in the vSphere Hardening Guide and apply to your environment. There’s not a lot of great tools out there other than scripting things yourself, so I’d make sure you’re comfortable with writing your own PowerCLI or VMware CLI scripts to apply to your environment and make sure you test them out ahead of time. You can still download PowerGUI here. If you prefer not to use a GUI for running scripts, that’s fine as long as you understand how to build out a robust Powershell server to run scripts in your environment and I’d recommend not using your own laptop. You’ll also need to make sure you have the right VMware PowerCLI package installed based on the version of vSphere you’re running in your environment.
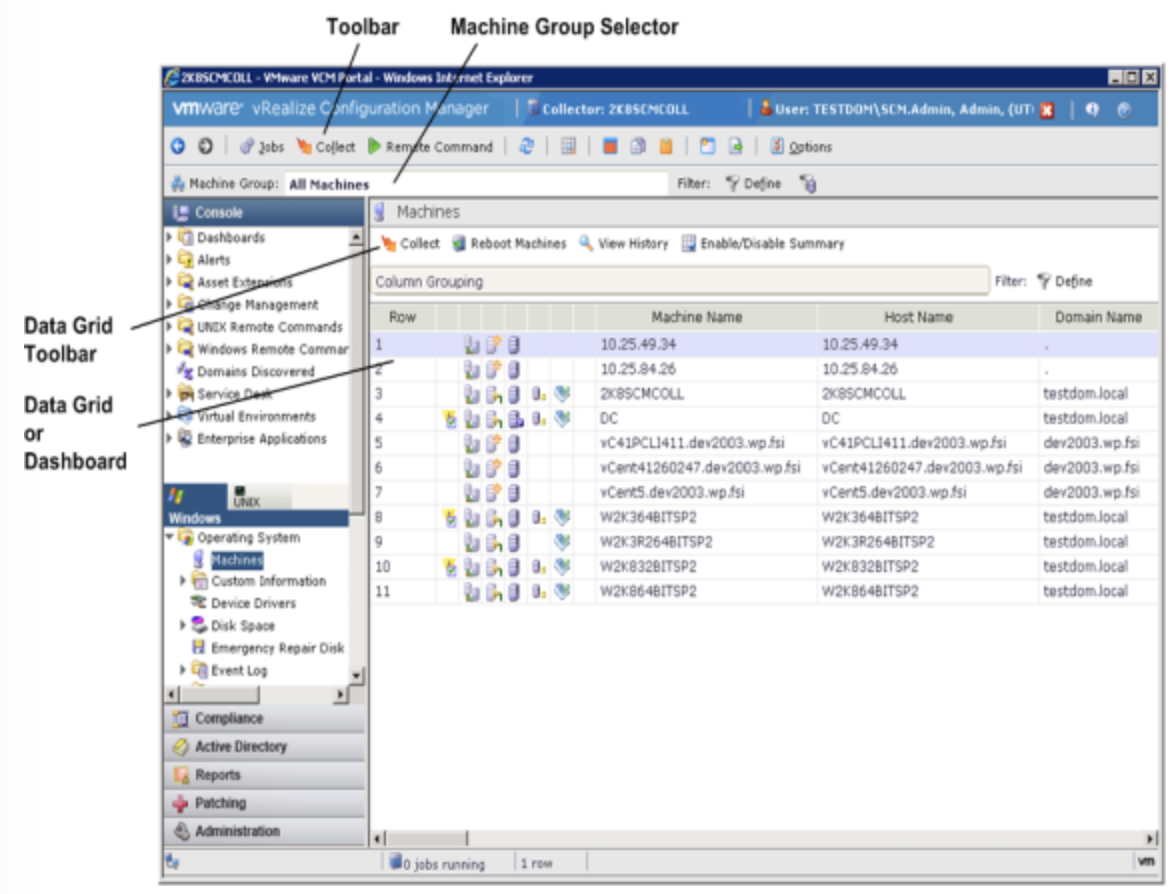
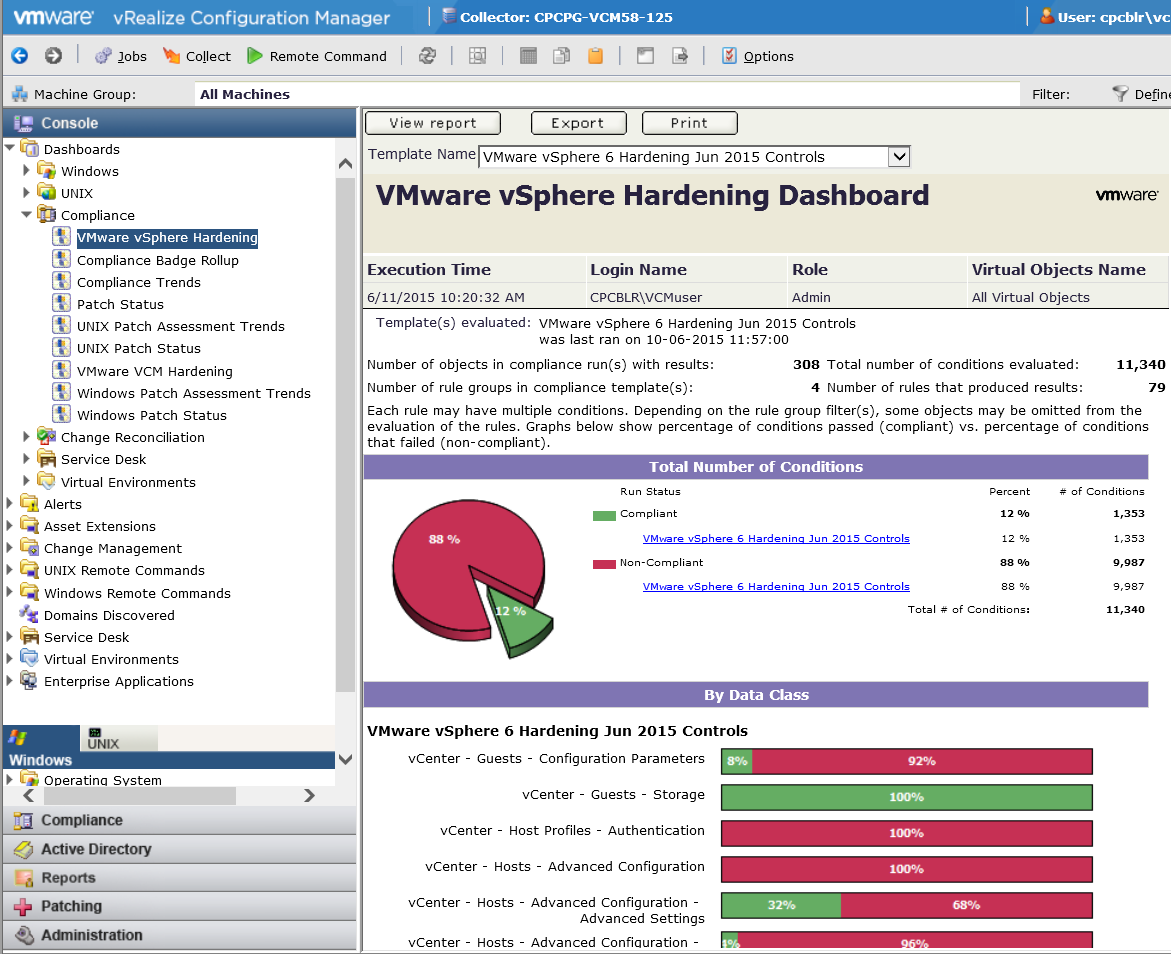
vRealize Configuration Manager
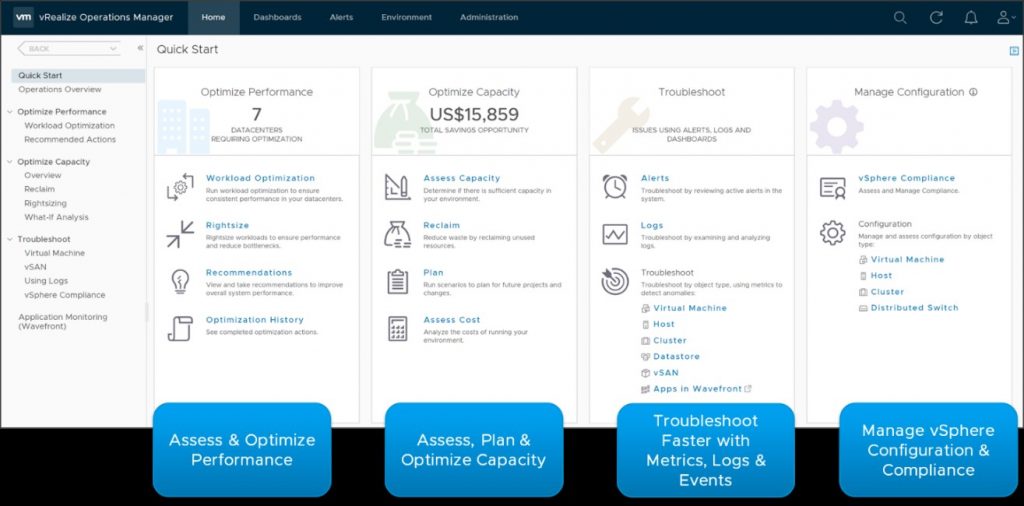
vRealize Operations Manager and vRealize Orchestrator
VMware vRealize Operations Manager delivers intelligent operations management with application-to-storage visibility across physical, virtual, and cloud infrastructures. Using policy-based automation, operations teams automate key processes and improve IT efficiency. Using data collected from system resources (objects), vRealize Operations Manager identifies issues in any monitored system component, often before the customer notices a problem. vRealize Operations Manager also frequently suggests corrective actions you can take to fix the problem right away. For more challenging problems, vRealize Operations Manager offers rich analytical tools that allow you to review and manipulate object data to reveal hidden issues, investigate complex technical problems, identify trends, or drill down to gauge the health of a single object.
VMware vRealize Orchestrator is a drag-and-drop workflow software that simplifies the automation of complex IT tasks. It integrates with VMware vRealize Suite and vCloud Suite® to adapt and extend service delivery and operational management capabilities. This allows for more seamless integrations with existing infrastructure, tools and processes.
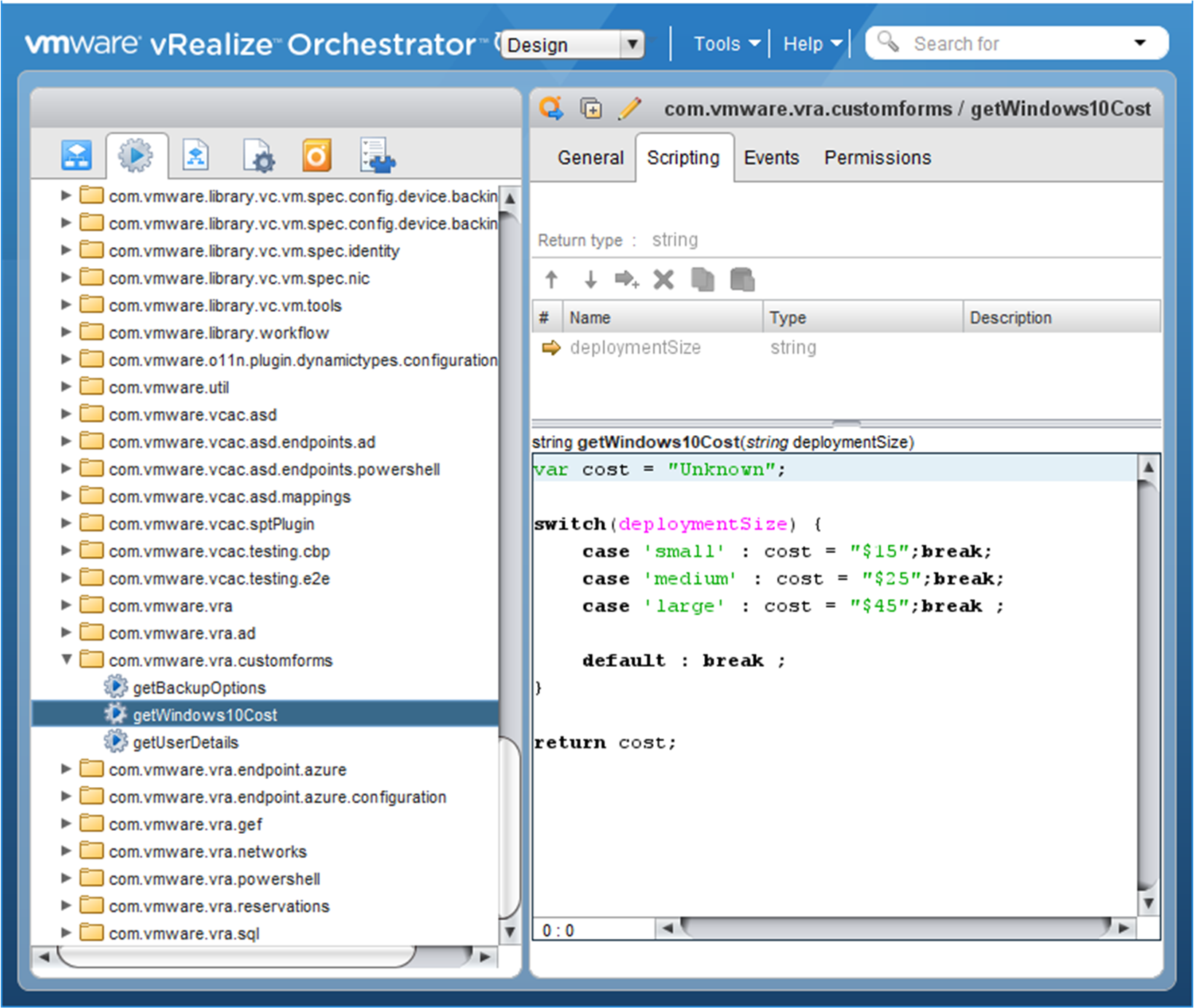
vROPs has the ability to report on vSphere Security Configuration Guide configuration parameters. This allows you to leverage the config options applicable to your environment within a policy and apply to your different vSphere environments to report on configuration drift. The challenge though is always around automating the remediation of those configuration drift parameters. vRO can integrate with vROPs in order to truly leverage the automated actions capabilities of vROPs. In other works, if you take the time to build out vRO workflows using the PowerCLI and VMware CLI scripts already provided in the vSphere Security Configuration Guide, you can leverage these workflows to automate the configuration drift of vSphere environment based on the vROPs Security Configuration Guide policy applied to your vSphere infrastructure. Based on my experience, I think VMware has an opportunity to build upon this. I’m working with our internal product management teams on a fling to start testing that will include a vROPs plugin that will leverage a pre-built set of orchestrator workflows. This will allow vSphere Operational and Security teams to use the automated actions capabilities of vROPs to ensure the vSphere infrastructure policy defined is applied at all times. This should reduce the amount of operational work required to keep your vSphere environment within policy and keep your security team’s scanning reports coming back with with a higher compliance rate.
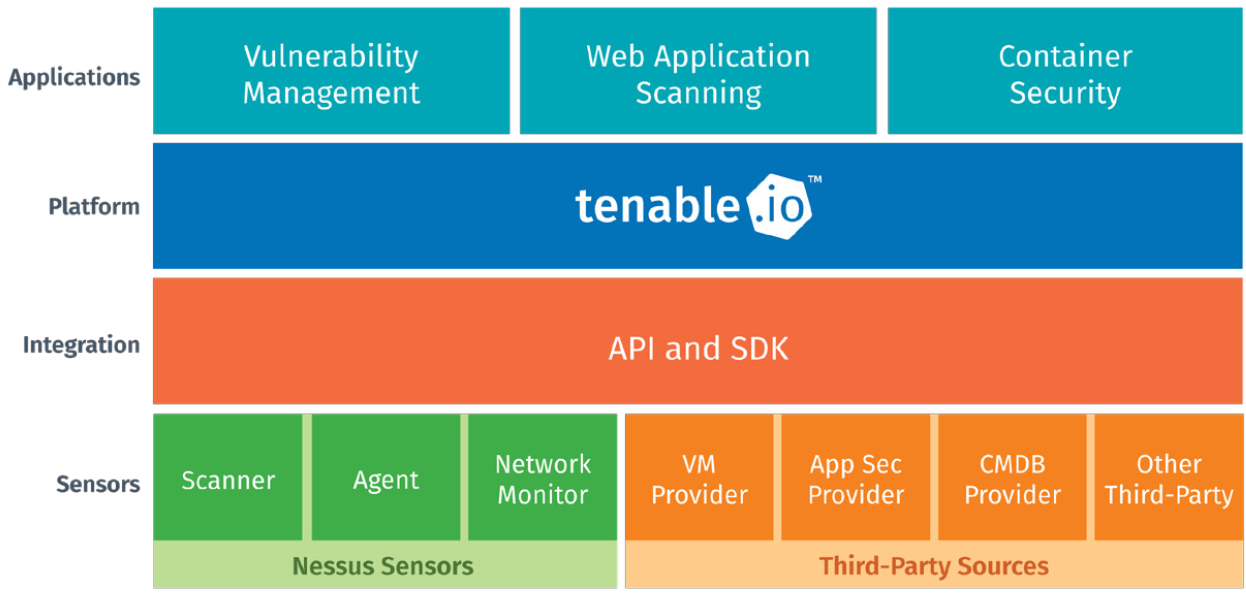
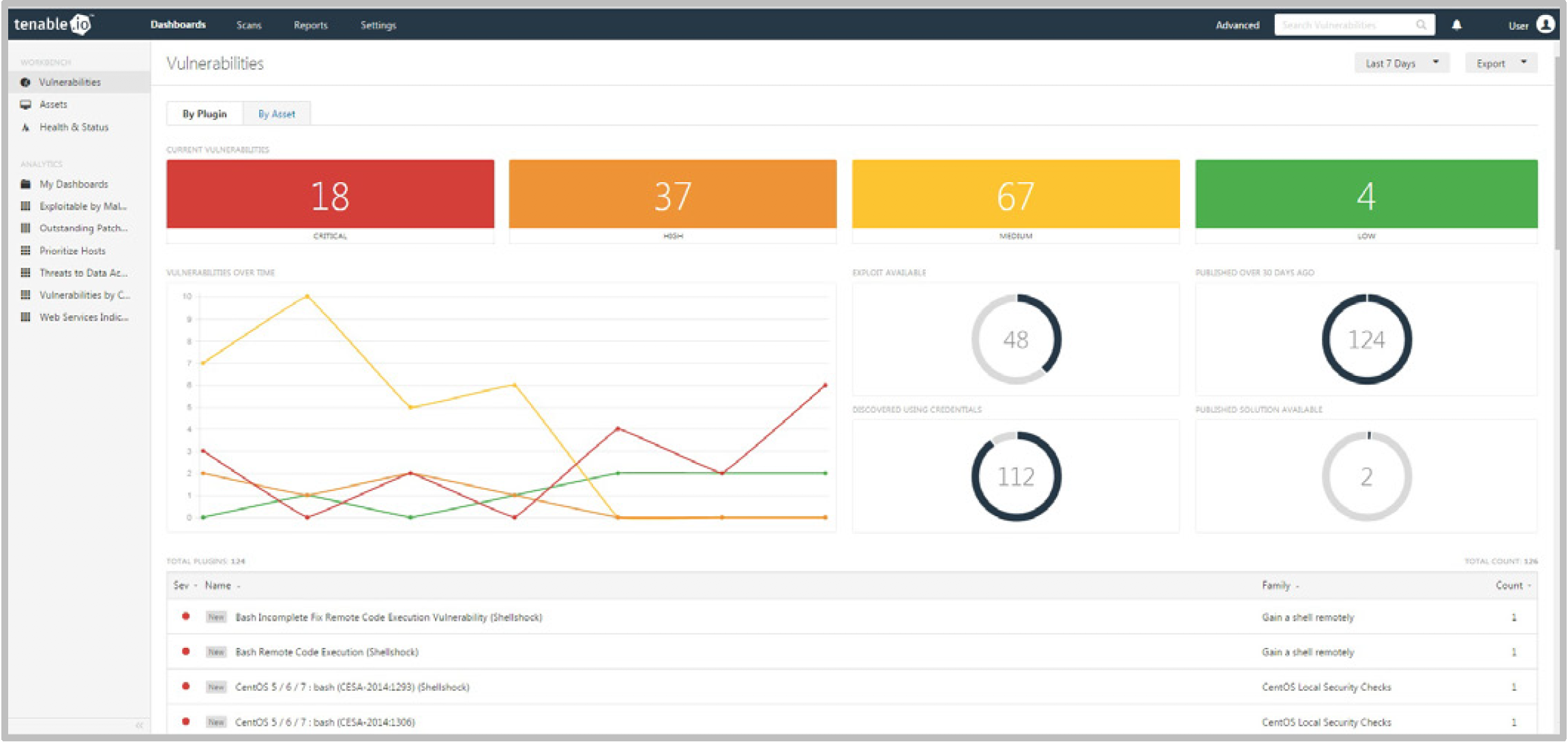
Tenable


Recent Comments